The Illusion of Trust Is the Real Security Risk
For years, enterprise security was built around a simple idea:
Once inside the network, you’re trusted.
That assumption is now the biggest weakness in modern systems.
Cloud computing, remote work, SaaS tools, APIs, and AI-driven automation have erased the traditional network perimeter. Attackers no longer “break in” — they log in, move laterally, and operate quietly.
This is why Zero Trust is no longer optional.
It’s becoming the default security mindset for organizations that want to survive 2026 and beyond.
What Is the Zero Trust Security Model?
The Zero Trust Security Model is a cybersecurity approach that assumes:
No user, device, application, or system should be trusted by default — even if it is already inside the network.
Instead of relying on location (inside vs outside), Zero Trust enforces continuous verification based on identity, context, and behavior.
Every request must prove:
- Who is making it
- What device is involved
- Why access is needed
- Whether the context is safe right now
Why Traditional Perimeter Security No Longer Works
The Old Model (Why It Fails)
- Strong outer firewall
- Weak internal controls
- Broad access once authenticated
This fails because:
- Credentials are easily stolen
- Insider threats are real
- SaaS and cloud apps live outside your network
- APIs don’t respect firewalls
Real pain point:
Most breaches today don’t involve malware — they involve legitimate access used maliciously.
Many of the cloud security failures we see today don’t happen because defenses are missing — they happen because trust is assumed too early. Modern cloud environments demand security models that account for identity abuse, misconfigurations, and rapid system changes rather than static perimeters.
Core Principles of Zero Trust Security
#1. Verify Every Identity
In Zero Trust, identity is the new perimeter.
This includes:
- Human users
- Service accounts
- APIs
- Devices
- AI agents
Every request must prove:
- Who is making it
- From where
- Under what conditions
#2. Enforce Least Privilege Access
Users and systems should have only the access they need — nothing more.
This limits:
- Blast radius
- Damage from compromised credentials
- Insider threats
Access is:
- Scoped
- Time-bound
- Context-aware
#3. Assume Breach
Zero Trust assumes attackers will get in.
The goal is to:
- Detect them early
- Limit movement
- Contain damage
This mindset shift is critical in 2026, where breaches are inevitable but disasters are not.
#4. Segment Everything
Zero Trust breaks systems into isolated segments.
If one segment is compromised:
- Others remain protected
- Movement is restricted
- Impact is minimized
Segmentation applies to:
- Networks
- Applications
- Cloud workloads
- Data access
#5. Monitor Continuously
Trust is never permanent.
Zero Trust relies on:
- Continuous monitoring
- Behavioral analysis
- Anomaly detection
Suspicious behavior triggers:
- Re-verification
- Access restriction
- Alerts or isolation
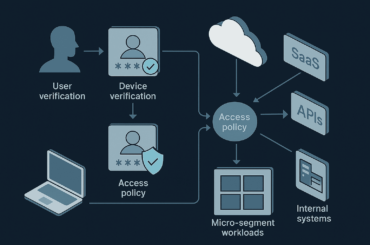
How Zero Trust Works in Real-World Environments
Zero Trust is not a single product.
It’s a security architecture built from:
- Identity and access management (IAM)
- Multi-factor authentication (MFA)
- Device posture checks
- Network segmentation
- Continuous logging and analytics
Each access request is evaluated in real time:
Who is requesting access? From where? To what? Under what conditions?
Zero Trust in Cloud and Hybrid Systems
Cloud environments make Zero Trust essential.
Why?
- No fixed perimeter
- Highly dynamic resources
- Identity-based access
- API-driven systems
In cloud security, Zero Trust:
- Protects workloads
- Secures APIs
- Controls service-to-service communication
- Limits misconfiguration impact
Zero Trust becomes especially important in cloud systems, where visibility, identity control, and blast-radius limitation matter more than traditional firewalls. Without disciplined cloud security practices, even strong Zero Trust policies can break down under scale.
Common Zero Trust Myths (Debunked)
“Zero Trust means trusting nothing ever”
Reality: It means verifying continuously, not blocking productivity.
“Zero Trust is only for large enterprises”
Reality: Small teams benefit even more due to limited security resources.
“Zero Trust is too complex”
Reality: Complexity comes from poor implementation, not the model itself.
Zero Trust vs Traditional Security (Quick Comparision)
| Area | Traditional Security | Zero Trust |
|---|---|---|
| Trust Model | Implicit | Continuous |
| Perimeter | Network-based | Identity-based |
| Access | Broad | Least privilege |
| Breach Impact | High | Contained |
Benefits of the Zero Trust Security Model
- Reduced breach impact
- Better visibility
- Stronger access control
- Improved compliance
- Resilience against credential abuse
Zero Trust doesn’t eliminate attacks — it neutralizes them faster.
When Should You Adopt Zero Trust?
The answer in 2026 is simple:
Now.
If you use:
- Cloud services
- Remote access
- APIs
- SaaS tools
- AI systems
You already need Zero Trust.
Final Takeaway
Zero Trust is not something you “install.”
It’s something you design for.
Organizations that succeed treat Zero Trust as:
- An architectural principle
- A risk-reduction strategy
- A long-term transformation
Those that delay usually learn the hard way.
FAQs
Zero Trust is a security model where no user or system is trusted by default, and every access request is verified continuously.
Because cloud computing, remote work, APIs, and AI systems eliminate traditional network perimeters.
No. It includes identity, device security, network segmentation, monitoring, and continuous verification.
No. It complements them by adding identity-based and contextual security controls.
It can be implemented gradually using existing tools, making it cost-effective over time.