Why Most Zero Trust Initiatives Fail
Zero Trust is widely discussed — but poorly implemented.
Many organizations believe they’ve “done Zero Trust” because they:
- Enabled MFA
- Bought a Zero Trust product
- Migrated to the cloud
Then a breach happens.
The problem isn’t Zero Trust itself.
The problem is treating it like a tool instead of an operating model.
This guide explains how Zero Trust actually gets implemented in real environments in 2026 — across cloud, SaaS, APIs, AI systems, and remote teams — without breaking productivity.
Step 1: Accept the Core Reality — You Already Have No Perimeter
Before any tooling decisions, leadership must accept this:
- Your data lives in SaaS apps
- Your users work remotely
- Your APIs are internet-facing
- Your systems talk to machines, not just people
Trying to “secure the network” first is a dead end.
Zero Trust starts with identity, not infrastructure.
Zero Trust is often misunderstood as a collection of tools rather than a security philosophy. Without understanding the underlying model — particularly why implicit trust fails in modern systems — implementation efforts tend to focus on controls instead of outcomes.
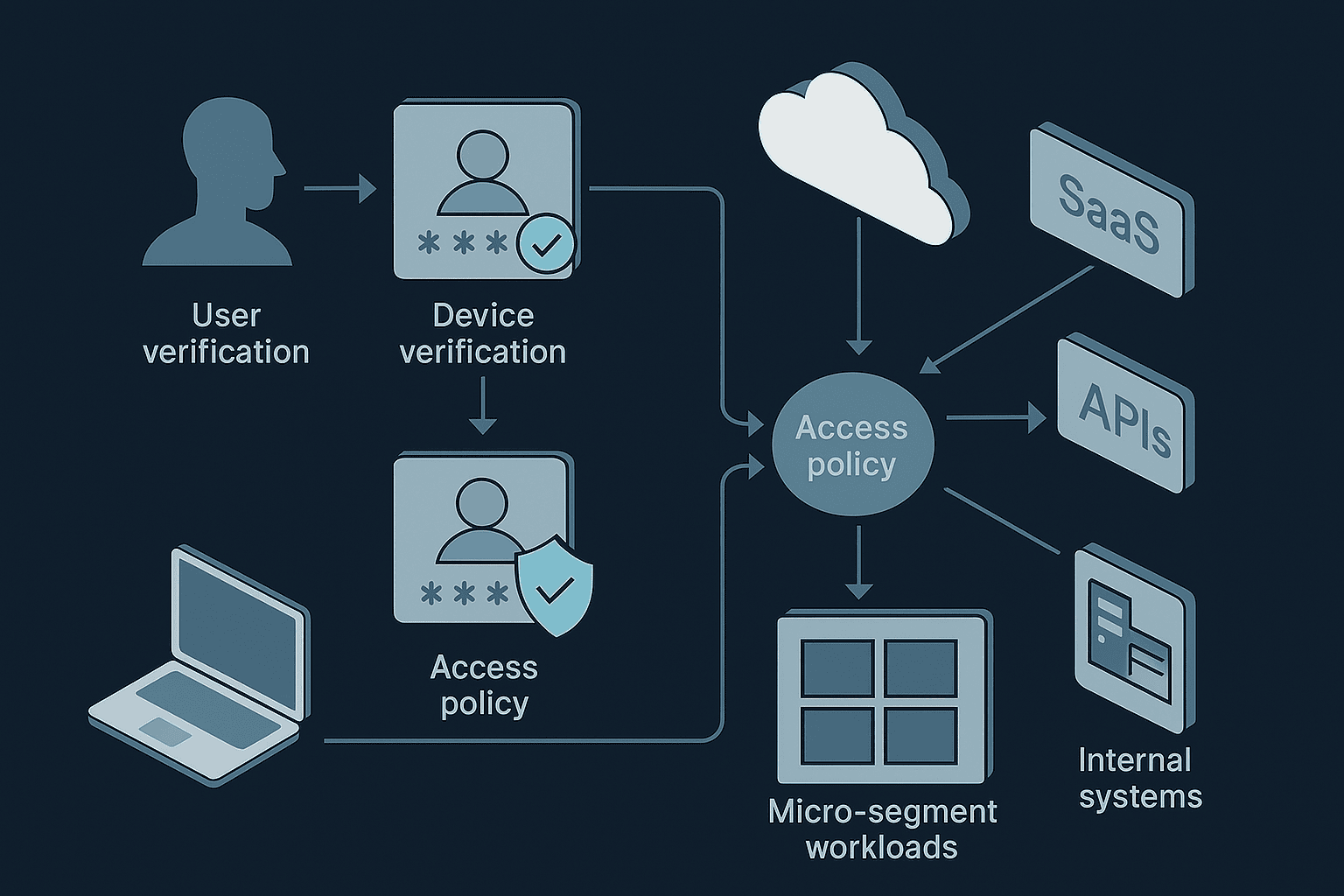
Step 2: Make Identity the Control Plane (This Is Non-Negotiable)
What This Means in Practice
Every access decision must be tied to:
- A verified identity
- A known device
- A clear policy
This applies to:
- Employees
- Contractors
- Services
- AI agents
- APIs
Key Implementation Actions
- Centralize identity (IdP as the source of truth)
- Enforce MFA everywhere (humans + admins)
- Eliminate shared credentials
- Introduce workload identities for services
Common mistake:
Securing users but ignoring service-to-service access — the fastest way to lateral movement.
Step 3: Inventory What Actually Exists (Not What You Think Exists)
Zero Trust fails when teams protect assumed architecture, not reality.
What You Must Map
- Users and roles
- Devices (managed vs unmanaged)
- SaaS applications
- APIs and internal services
- Data flows between systems
This step is uncomfortable — and essential.
You cannot enforce least privilege on assets you haven’t acknowledged.
Step 4: Implement Least Privilege — Gradually and Intelligently
Why Least Privilege Breaks Teams
Done aggressively, it:
- Blocks workflows
- Creates ticket storms
- Breeds resistance
How to Do It Properly
- Start with read-only access tightening
- Apply time-bound permissions
- Use role-based + context-aware policies
- Monitor before enforcing
2026 reality:
Static roles are insufficient. Access must adapt to risk signals.
Step 5: Secure Devices as First-Class Citizens
In Zero Trust:
A compromised device is the same as a compromised user.
Practical Controls
- Device posture checks (OS, patch level)
- Block unknown or jailbroken devices
- Separate policies for BYOD
- Continuous reassessment, not one-time checks
No device trust = no access — regardless of who logs in.
Step 6: Apply Micro-Segmentation Where It Actually Matters
Micro-segmentation doesn’t mean slicing everything.
It means:
- Isolating critical systems
- Restricting east–west traffic
- Limiting blast radius
High-Impact Targets
- Databases
- Admin interfaces
- CI/CD pipelines
- Production APIs
This single step drastically reduces breach impact.
Step 7: Zero Trust for Cloud, SaaS, and APIs
Cloud
- Identity-based access (not IP-based)
- Service-to-service authentication
- Scoped permissions per workload
SaaS
- Conditional access policies
- Session risk evaluation
- Continuous authentication
APIs
- Mutual authentication
- Token scoping
- Rate and behavior monitoring
APIs are now the largest attack surface — Zero Trust must include them.
Cloud environments introduce unique risks because identity, configuration, and visibility matter more than network location. Many Zero Trust rollouts struggle here simply because cloud security fundamentals are weak to begin with.
Step 8: Logging, Visibility, and Continuous Verification
Zero Trust is not “set and forget.”
You need:
- Centralized logging
- Behavioral baselines
- Anomaly detection
- Real-time policy enforcement
If you can’t see it, you can’t trust it.
Step 9: Human-in-the-Loop (Critical for 2026)
Automation without oversight is dangerous.
Zero Trust implementations must include:
- Manual approval paths for high-risk access
- Audit trails
- Clear escalation workflows
Especially important when:
- AI systems trigger actions
- Access policies change dynamically
Step 10: Measure What Actually Matters
Meaningful Metrics
- Time to detect unauthorized access
- Lateral movement attempts blocked
- Privileged access duration
- Incident blast radius
Avoid vanity metrics like “number of policies created.”
Common Zero Trust Implementation Failures (Learn From Others)
Buying tools before defining architecture
Ignoring legacy systems
Treating Zero Trust as an IT-only initiative
Breaking productivity without change management
Assuming Zero Trust = zero breaches
Zero Trust reduces impact, not existence, of attacks.
What a Mature Zero Trust Environment Looks Like in 2026
- Identity-driven access everywhere
- Continuous verification
- Minimal standing privileges
- Limited blast radius
- High visibility
- Humans still accountable
It feels boring — and that’s a good thing.
Final Thoughts: Zero Trust Is a Journey, Not a Deadline
There is no “Zero Trust completed” checkbox.
Organizations that succeed:
- Iterate
- Measure
- Adapt
- Educate continuously
Those that rush usually end up rebuilding from scratch.
FAQs
Most organizations roll out Zero Trust incrementally over 6–18 months depending on size, complexity, and legacy systems.
No. Smaller organizations often benefit more because Zero Trust reduces the blast radius of attacks that could otherwise be fatal.
No. Firewalls still exist, but Zero Trust shifts enforcement to identity and context rather than network location.
Yes. Zero Trust is particularly effective in cloud, SaaS, and API-driven environments.