In 2026, cloud security failures no longer make headlines because they’re shocking, they make headlines because they’re predictable.
The pattern is familiar:
- A valid credential is abused
- A misconfigured service goes unnoticed
- An alert fires too late
This isn’t because teams don’t care about security.
It’s because cloud security has outgrown traditional defenses.
This guide focuses on cybersecurity best practices for cloud systems in 2026 — grounded in how attacks actually happen today.
Why Cloud Security in 2026 Is Fundamentally Different
Cloud systems are now:
- AI-integrated
- API-driven
- Highly automated
- Distributed across services and regions
This creates a harsh truth:
In 2026, attackers don’t “break in” — they log in.
Security is no longer about blocking access.
It’s about controlling identity, context, and blast radius.
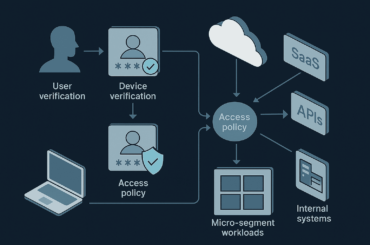
#1. Identity Is the New Attack Surface
Credentials are the #1 entry point in modern cloud breaches.
In 2026, attackers:
- Steal tokens instead of passwords
- Abuse service accounts
- Exploit over-permissioned roles
- Move laterally using legitimate access
What Actually Works in 2026
- Enforce least privilege by default
- Use short-lived credentials
- Eliminate shared admin accounts
- Apply context-aware access (device, location, behavior)
If identity isn’t locked down, nothing else matters.
#2. Zero Trust Is No Longer Optional — It’s Baseline
Zero Trust in 2026 isn’t a buzzword — it’s survival.
Modern Zero Trust Means:
- Never assume internal traffic is safe
- Continuously verify identities
- Segment workloads aggressively
- Monitor trust dynamically
Static trust models fail in environments where:
- AI agents access systems
- Services talk to services
- APIs scale faster than humans can track
#3. Secure Configuration Is a Continuous Process, Not a Setup Task
Most breaches still start with misconfiguration.
Open storage, exposed APIs, permissive network rules — these issues don’t come from negligence. They come from scale and speed.
Best Practices for 2026
- Security baselines as code
- Continuous configuration scanning
- Automated remediation
- Drift detection as a security signal
If configuration isn’t monitored continuously, it’s already outdated.
#4. Encryption Alone Is Not Enough — Key Control Is Everything
Encryption is table stakes in 2026.
What separates secure teams from vulnerable ones is key governance.
Key Best Practices
- Centralized key management
- Strict access policies
- Regular key rotation
- Monitoring key usage anomalies
Attackers don’t break encryption — they steal access to keys.
#5. Assume Breach, Design for Containment
In 2026, the question isn’t if a breach happens — it’s how far it spreads.
Containment-Focused Design
- Environment isolation
- Network segmentation
- Scoped service permissions
- Controlled east-west traffic
A well-designed system turns a breach into:
an incident, not a catastrophe.
#6. AI-Driven Threats Require AI-Aware Defenses
AI didn’t just change how companies build systems —
it changed how attackers operate.
In 2026, attackers:
- Use AI to test configurations
- Automate credential abuse
- Adapt faster than static rules
Defensive Shift
- Behavior-based monitoring
- Anomaly detection over signatures
- AI-assisted investigation
- Human-in-the-loop decision making
Security must evolve at machine speed.
#7. Observability Is Security
If you can’t see it, you can’t secure it.
Modern cloud security requires:
- Deep visibility into identity usage
- API activity monitoring
- Cross-service correlation
- Actionable alerts, not noise
Silence does not mean safety.
It usually means blind spots.
#8. Secure the Software Supply Chain
Cloud breaches increasingly originate from:
- CI/CD pipelines
- Third-party dependencies
- Compromised build systems
2026 Best Practices
- Minimal pipeline permissions
- Dependency integrity checks
- Secret scanning
- Build activity monitoring
A compromised pipeline deploys attackers faster than humans ever could.
#9. Design for Human Error
Human error hasn’t disappeared in 2026 — it’s just faster.
Security systems must:
- Prevent risky defaults
- Require confirmations for sensitive actions
- Alert early, not after damage
- Enable fast rollback
The best security systems expect mistakes and limit their impact.
#10. Test Security Like an Attacker Would
Annual audits don’t reflect real threats.
Effective 2026 testing includes:
- Continuous attack simulation
- Credential compromise drills
- Lateral movement testing
- Real cloud attack paths
If you don’t test your defenses, attackers will — for free.
The Cloud Security Mindset for 2026
The most secure teams don’t chase tools.
They build security systems that adapt.
Cloud security works when:
- Identity is controlled
- Access is contextual
- Failures are contained
- Visibility is continuous
- Humans stay in the loop
Final Takeaway
In 2026, cloud security isn’t about perfection.
It’s about resilience.
Design systems that assume:
- Credentials will leak
- Configurations will drift
- Humans will make mistakes
When security is built for reality, the cloud becomes safer — not scarier.
FAQs
The biggest cloud security risk in 2026 is identity abuse, not infrastructure attacks. Most breaches happen when attackers gain access to valid credentials, over-permissioned roles, or service accounts rather than exploiting software vulnerabilities.
Cloud security in 2026 is identity-centric, AI-aware, and automation-driven. Traditional perimeter security is no longer effective because cloud systems rely on APIs, services, and machine identities instead of fixed networks.
Yes. In 2026, Zero Trust is the baseline, not an advanced strategy. Modern Zero Trust focuses on continuous verification, least privilege access, workload segmentation, and real-time behavior monitoring across cloud systems.
No. Cloud providers secure the underlying infrastructure, but customers are responsible for securing identities, data, access permissions, configurations, applications, and compliance. This shared responsibility model still causes many cloud security failures.
AI increases both attack speed and defense capabilities. Attackers use AI to automate credential abuse and configuration discovery, while defenders rely on AI for anomaly detection, behavioral analysis, and faster incident response.